-
-
GDPR Information
We acknowledge that some of the data on this website may be outdated, and we recognize the introduction of new regulations, including GDPR. We are committed to respecting user privacy and will process all deletion requests, provided they originate from the verified account in question. Additionally, users can request the complete anonymization of their content using the built-in tool available in their account settings. Please understand that your request might not be processed immediatly or even in a short delay. But they will be approved as soon as we notice them. Feel free to reach with us for further informations about your rights.
-
Happy B-day to me
Hey samster ! Sorry I am a bit late, but I wish you a very happy birthday !
-
UnstucK changed their profile photo
-
myg0t Archives, available 14 years later !
The Private Area of the myg0t archive remains hidden from public view, as it contains sensitive and confidential information. This section includes numerous private code snippets, many of which, while outdated, were never intended for public release or distribution. Out of respect for the original contributors and the nature of this content, I have chosen not to make it publicly accessible. However, if you previously had an account on myg0t and can provide verifiable proof of ownership (good luck with that), I am open to restoring your access. All restored accounts will retain their original group and rank assignments. For example, if you were a myg0t staff member, you will have access to the Private Area based on your assigned staff level. If you have any questions or wish to request access, feel free to reach out.
-
FBI - Valve Software_Axel_Gembe.pdf
FBI - VALVE SOFTWARE - AXEL GEMBE.pdf
-
February 16, 2004 - "Initial DaGuy email"
Hello Gabe, I'm very sorry about what happened with HL2. I want to explain a few things. I was in your network for ~6 months, watching your development process, which was very interesting. Yes, I am the hacker, no, I didn't distribute HL2. Beginning of September, I was on LCIRC exchanging some info with a friend that works on a project with me, but my connection was being watched by the myg0t guys. I only found out later that LCIRC is full of myg0t people and I have been sniffed. So, basically they got WebMail & VPN passwords by me being foolish about this stuff. I don't know exactly what they installed, but the modified RemoteAnywhere and the Keyloggers were not installed by me, I only installed a self-developed SourceSafe client/server system on 2 Win32 PCs to keep my HL2 up to date, and I later set up backdoors on 2 of the linux routers, and also ported my SourceSafe client-server system to Linux to be able to download faster. I think you found those, but the rest was not installed by me. If you got any interest in my VSS utility, mail me and I'll send the sourcecode, they give a huge speedup compared to VSS or SourceOffSite. Well, I learned from this incident that I should not transmit unencrypted passwords for such important things. I wanted to help you people get to know the truth by writing this mail, and I never intended to harm you. I only didn't tell you I was in your network cause I was afraid to get kicked out, I just wanted to observe the HL2 development process, cause I'm a hobby developer myself and a big an of HL2, let's just say I'm amazed by the capabilities of your team. Well, thats it. Just so there is no confusion about my identity, I'll just attach some document I got thats not available elsewhere cause myg0t probably only had time to check out very few stuff (~15 days). tf2/scripts/objects.txt docs/e3_2003/e3 final.rtf Thank you for your time, - Da Guy
-
February 18, 2004 - "RE: So, do you believe me?"
On Tue, 17 Feb 2004 Gabe Newell <[email protected]> wrote: >I get a couple of hundred spam messages a day, which sucks. Ooh, that's bad 🙂 I usually use addresses I dump later for most stuff, but I assume you can't do that as easily. >I downloaded the VSS client, but I haven't had a chance to look >at it >yet. I need to run home to deliver chicken yakisoba to the starving >children, but I'll take a look at it tonight. yaki="fried" soba="buckwheat noodles" with chicken? Mmmmm, I like asian food, except sushi 🙂 Thx for having a look at it, but don't if you're too busy, just throw it at someone else. I imagine you'd have to check the source for nasty backdoors, but be assured there are none. Anyways, I'd just like that tool to be used, cause I though its pretty kewl tool, but I have no use for it anymore cause I use cvs and/or BitKeeper for my programming work. >So it's cool that you are clearing up the mystery for us, but why are >you >doing it? Does knowing that you should have done this long time ago count? Also I wanted to know if you'd still want to catch me when you know that the real hacker didn't distribute HL2 but was getting sniffed. What would you have said if I told you of this in time ? Well, I also didn't like what the people releasing HL2 have done, so I want to disclose my part of the story. But I also gotta say that you people didn't do too much at that time for your network security (I think you were just too busy with HL2), even after october, I had access to 4 Valve-owner systems, 1 being a team-server, 1 being the adminmod sf.net servers, 1 being your webserver (but someone kicked me out there and left messages on the FTP for me) and 1 being a MySQL server where I could have added malicious stuff into /root/.bash_history or into a .bat/.cmd file in startup folder). So, my point here is: get a dedicated security person for the network, someone who only is there to administrate/audit networks. Also you should consider auditing the steam source sometimes, because that is critical infrastructure. In a network I administer we have all critical infrastructure stuff behind a second firewall that also runs an IDS, theres 1 internet facing host running Linux & WebServer, and it also runs a self written program that checks for anomalies in TCP traffic and blocks offending hosts at both firewalls. Also I want to note that I wrote me some kind of sourcecode encryption tool, that also is a build system, which will produce signed self-checking binaries using RSA private/public keys, maybe you could also think about using more secure build system. What I'd also like to know is what was installed on your PC, cause I never even had access to it. When you wrote to hl2.net forums, you only mentioned a few of my tools, but the RemoteAnywhere and the keylogger were not installed by me. Basically I only did do the minimum required stuff, which was crack the PCS (I used the "Build" - "" Administrator account), crack MD5 hashes using rainbow tables (took a few seconds to get most of em), g get access to some good headless Win32 machine to use first (your compiler farm), get angry about sourcesafe speed, code my own tool, get HL2 fast but not fast enough, get access to some linux host (lists.valvesoftware.com, which was later cleaned, then I used Alfreds profiler host), port my tool to Linux and finally get HL2 fast enough. I've always used P4Win from a .cmd file, cause that was fast enough over Internet. After I accomplished this, I leaned back and watched your development process, which is the most amazing thing I ever saw. Also I wanted to write you because lots of people claim they hacked you, like that Anon fag, but all this is based on a few passwords and some other info that was sniffed from me. I really shouldn't have transmitted that stuff in cleartext. Well, write me if you wanna know anymore facts or other details, I think I can give you answers to much questions. - Da Guy PS: as much as I'd like to disclose my identity, I still fear getting caught for this, though I didn't want to harm anybody. Think about it, someone else could have entered your system as easily as me. But still I acknowledge that this was my fault & your fault, my fault for transmitting passwords in clear text and even entering those systems, your fault for not securing them properly.
-
February 19, 2004 - "RE: So, do you believe me?"
On Thu, 19 Feb 2004 Gabe Newell <[email protected]> wrote: >So how much do you know about the jerks who actually did the leak? I can only say 1 name that I know of, which is SourceX. Hes the owner of LCIRC (which I didn't know before the leak), and he owns all the boxes LCIRC is hosted on. This breakin was clearly done using sniffed data from me and SourceX is the only one with the capabilities, the knowledge and the motives to have sniffed me there (I now even know of other people that got sniffed there, but I was stupid and trusted SSL to keep me secure). Also I am sure I didn't exchange the passwords and other info elsewhere, and I personally know and trust the guy I've given them to. And seeing that most info points to SourceX and myg0t, it must have been them. I even think the Anon guy might have been from myg0t and/or known to myg0t. >Was there some reason they were targetting you in particular? I think so, I had access to valvesoftware.com, and they didn't have. Also I don't think this wa targeted by them, I just think they are bad guys and watch everything thats being done on their server, so they saw me exchanging that info with my co-worker, saw valvesoftware.com, checked it a little more and saw that it was complete login data and some misc other info. And I thought I'd have to hide from FBI and/or other agencies 🙂 >Gabe Problem with this is that SourceX / whoever did this knows my real nick/ip and they will probably say "We didn't do this, his is the guy that did the breakin" or probably "that guy gave us access". And also there would have to be evidence. If you'd crack down on Hitman or some others of those for distributing the leak, he'd probably tell you the real people behind it, but I can only that it was done by myg0t. I might get you some more evidence, but that would require you to give me a written confirmation that you will not prosecute me for any hacking actions before may 2004 (you can exempt copyright violations/other stuff from this in case you don't trust me). Also I'd like to ask, you don't happen to search a Programmer / Security specialist who recently lost his job ? I program small games, in OpenGL/D3D which work on Linux and Win32. I also code small utilities for my hacking / pentesting / network admin usage, and I'm pretty advanced when it comes to network security. Think about it, I'd really like to work for someone like you. Also you didn't answer my last question, which was about what you would have done if I had told you that I was in you network early, like jan 2003. In case you're too busy to answer my stuff, direct me to someone else (preferrably alfred, if hes got the time, he got knowledge of the stuff I installed on the linux pcs, and hes the one whose stuff I always admired the most, cause he does stuff for the linux community) Please try to answer some of my questions, I try to answer yours, too. - Da Guy
-
February 28, 2004 - "RE: So, do you believe me?"
On Fri, 27 Feb 2004 Gabe Newell <[email protected]> wrote: >Aagh. Crack week. We're going through planning for E3 and showing >off >the XBOX version for the first time. Microsoft is getting pretty >hungry >for anything to make the XBOX look competitive with the PS2. > No problem, I understand you are a busy man, especially when Bill wants his HL2 for his XBOX 🙂 Does the XBOX even support Misc by default, or will you have to play it with controller? >Were you kidding about working here? You certainly impressed us >with >your skills. We've hired a lot of people from the community, and >I >guess in a funny way this would be more of the same. If you were >teasing, ha ha, you got me. No, I wasn't kidding, though the whole offer sounded strange 🙂 But I trust your words. I am able to move, and I can start working any moment. I really want to work in a team as skilled as yours (and I would consider myself skilled, too, but where I live there are no good IT jobs, that's why I'm unemployed atm.). I'll send you some kind of resume and a few samples of contrat and/or hobby work I've done (Don't judge me by the quality of the SourceSafe tool, I've written it in only 2 days, but it works well :). So, in any case, when could I expect this to happen ? I might have to do to the army else, if I don't move out of the country, and having to go to the army sucks 🙂 Well, I probably can't shake hands in office with you tomorrow, but I'l like to get this done ASAP is possible, because of the army issue 🙂 Also, you got some serious butt-kicking to do, so your admin upgrades ftp.valvesoftware.com like I told you last time, casue there are 2 public exploits against Serv-U 4.1, and there are also 2 unreleased private exploits which work up to 5.0.0.4 (I have a few connections, and write some exploits myself, too). Also, may I officially pen-test your network the next few days if I'm bored ? I'll tell you all the info I found 🙂 I did this for RWS once (with permission) and I gotta say they are pretty damn secure, but they don't host any big servers like you do for Steam. Well, I really hope you hire me, I'm no bad guy, just a little misguided 🙂 >Gabe
-
February 29, 2004 - "RE: So, do you believe me?"
On Sun, 29 Feb 2004 Gabe Newell <[email protected]> wrote: >Yep. I appreciated the heads up on that. No problem, I can also inform you about possible security holes, cause I have quite a bit of insight into the hacking/cracking underground. Well, what do you think about me working for you ? If you want the resume first, tell me. I would be happy if I didn't have to search for a job anymore.
-
March 8, 2004 - "RE: So, do you believe me?"
Right now I'm assuming that our webserver and our FTP server are compromised. We're building new machines from scratch to replace them, and not getting too worried about what's on there until we swap them out. The link, ftp://132.230.1.7/incoming/to_valve.rar, you sent doesn't appear to work (no files in the directory). We pay for all interview related expenses (travel, hotel, food, etc...) as well as relocation expenses (pretty standard for the game business). Gabe -----Original Message----- From:[email protected] Sent:Saturday, March 06, 2004 To:Gabe Newell Subject:RE: So, do you believe me? >I'll try to be more prompt in my replies. May I ask what your definition of prompt is? 🙂 If my intents weren't to clear this thing up, I could have already taken over your FTP server. Also I'm sure I'm not the only one who got the 5.0.0.4 Serv-U exploit. I even modified it to work with enabled Win2k3 stack protection. I understand that you had problems with Stream and that you are probably very busy, but you should really get someone to patch this hole, because it's only a matter of time until the exploit goes public, and Rhinosoft hasn't released a patch for this. Maybe I should breakin and patch your FTP ? 🙂 Did you have a chance to look at my samples yet, and more importantly, are they still on the server ? Well, I don't have time to write a longer email, cause I got a Peer 2 Peer network to test / get stable.
-
March 30, 2004 - "axel - resume.html"
Axel Gembe Objective: Network Administrator / Programmer Summary Experiences with administering and securing Linux, Windows, and BSD based networks Experience in Visual C++, GNU C++, Pascal, BASIC, with focus on network, system and secure programming Ability to develop custom security solutions, based on free IDS systems and self-written anomaly detection systems/firewalls Ability to audit networks/software for common problems like buffer overflows, etc... Teamwork with multiple security teams and/or version control using SVN, CVS, VSS and a little Perforce Experience with cross-platform development on Win32/Linux and knowledge of the issues involved Experience Network Administration / Security: Network Administrator at [REDACTED] since 5 years. During that time not a single security issue occurred, though numerous attempts were observed. Server Administrator at PCom (German ISP) for 1 year, and for several other small companies. Created an anomaly detection system and a firewall for securing those companies, based on iptables, tepdump and some self-written analysis software. Contributed numerous fixes for the software I use to the Debian project, for example exim, debianutils, taper and vrum. Experience with setting up 99% uptime services with full backup, UPS, backup servers and RAID disks. Wrote various log parsing tools to diagnose fire detection systems. Implemented in a CGI that outputs a graphical representation of the data streams. Experience with setting up secure VPNs using VTum or IPSec Programming: Wrote a remote administration toolkit that can be used to notify about unusual events automatically or just administering the server Wrote a game engine that can display terrains based on the ROAM paper ( by Mark Duchineau, available here ), has its own windowing system, and can make use of 3DNow! processors. This is more of a test, cause I only got a test game for the engine. Wrote exploits for various flaws like buffer overflows, integer overflows and more. Also I wrote various tools to automatically test software for these flaws. Wrote a fast file synchronization algorithm using MD5 sums, which is also used in the SourceSafe client I wrote. Ability to quickly learn new programming language Relevant Work History 1999-pres. Network Administrator at [REDACTED] Germany 1997-1998 Server Administrator at PCom, Germany 1995-1998 Freelance webdesigner / programmer for all kinds of projects Education I don't really have any relevant education, in school I only learned really odd stuff, like how computers in the 80ies worked or Turbo Pascal
-
March 30, 2004 - "FW: So"
Attached:resume.rar (54 KB) Here is Axel's resume. -----Original Message----- From: [email protected] Sent:Tuesday, March 30, 2004 To: Alfred Reynolds Subject: RE: So On Mon, 25 Mar 2004 Alfred Reynolds <[email protected]> wrote: HTML is fine. A microsoft word doc wouldn't hurt either. Ok, here it is: ftp:///ftp.uni-freiburg.de/incoming/resume.rar password is "forvalve"
-
March 25, 2004 - "Da guy interview"
We had a phone interview commencing at 11:03am PST on 03/26/2004 with someone claiming to be the person that hacked valve (daguy). He contacted me on my phone extension in my office (extension 100). His initial contact was via na IDSN connection into his PC. He had trouble with the connection (bad voice quality) so we terminated that call and he rang us back via another line. He said this line was his phone line. The second call commenced at 11:13 am PST. I spoke with him briefly when I answered the second call and introduced Greg Coome. At this time Greg Coomer, Matt Bamberger, Yahn Bernier and myself were in the room. Greg introduced himself and said that it was unusual to not know his name. Daguy then stated his name was "Axel Gembe" and that he was from Germany. Greg then explained how the interview would proceed and then passed him off to Matt Bamberger. Matt asked Axel a series of technical questions related to programming. He asked him what projects he has worked on before, how large those projects where and what problems they had and how he solved them. They also discussed source control and some issues about it. Axel also mentioned creating a remote administration program and discussed some issues with writing it and maintaining it. Once Matt had finished his questioning I was introduced to him. I quickly introduced myself and asked him if he would like to talk about some generic technical questions I had prepared or whether he wanted to go straight to talking about how he hacked us. He was eager to talk about the hacking event. My first question was simply how he did it. He then went on to describe how he infiltrated our network and the various programs and exploits he used. The details are as follows. He entered the network via the tangis.com machine. He claims to have used an account with an empty password to get on the machine initially. Once on the machine he exploited the web server with a remote CGI exploit to escalate his account privileges. One he had control of tangis.com he made use of the trust relationship on the firewall to scan our internal LAN network. He found a machine (a "distributed compiler" machine to use his words) that he claims had another blank password. He used that account to enter the machine. Once on this machine he used a cracking tool to attack the password database on the Primary Domain Controlled (PDC) and extract user accounts and passwords. Once he had harvested some passwords he used these to get on various workstation machines, he mentioned my workstation in particular. He also used VSS to gain access to our HL2 content and perforce to get our source code. He said that he got onto "jeeves" (the name of the perforce server) and the ip addresses 207.173.178.176, 207.173.178.173 and 207.173.178.12 (.12 is the ip address assigned to "jeeves"). Perforce is a source control system we use. I then asked him about any linux boxes he may have compromised. He described how he used a SSH buffer overflow exploit on one of the machines to gain access. He also claimed that one of the accounts on the machine had the same password as an account on the PDS (and that he used that). He then said he installed the "adore" rootkit onto the machine to mask his presence and used the "vrun" application to create a tunnel between his PC and our server. He said that he created the "hl2roxx" directory on one of our machines. I mentioned I found a ".bla" directory and he said that he had also created that directory. He also said he used a custom application to sync to our VSS tree across this vtun tunnel. Initially he used this application on a windows machine (he did not mention which one specifically) but he said that was too slow so he then ported the application to run on our linux machines. Next I asked him how HL2 had been leaked. He claimed that he had been discussing his break in of valve on IRC with a friend and he suspected the owner of the IRC server to be monitoring his chat. I asked him if he was still on our network (or had been in our network post October 1st 2003) and he said that he had compromised our FTP server since then but had been unable to get back across the firewall onto our internal LAN. I then thanked him for his time and passed the phone back to Greg Coomer. Greg asked him to send us a more detailed resume and told him that he would talk to Gabe early next week and get back to him. Greg also asked when he was available to fly over here so we could interview him in person. He said that he could come when we wanted him to as he could do any work he needed to do remotely. At this point we hung the phone up. The time was approximately 11:40am. The detailed information he provided to us fits with the information we discovered during our investigation of the break in. He provided us with details that we (Valve) have only revealed to the FBI (such as the names of the directories created on the machine and the use of the "vtun" and "adore" applications).
-
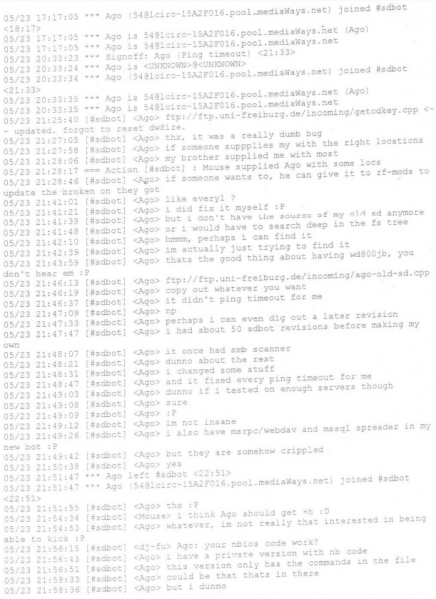
September 25, 2003 - "Unnamed Chatlogs"
-
May 4, 2004 - "Re: Intrusion into Valve Software Netwoork"
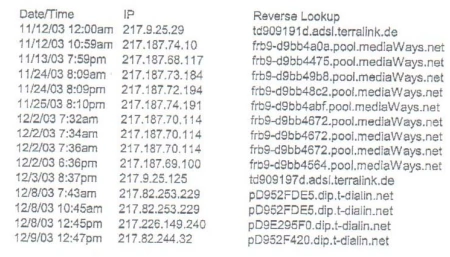
Summary of Investigation Valve Software, located in Bellevue, Washington, USA, creates, produces and sells popular Internet-based computer video games. One of these games is Half-Life, an immensely popular game with sales exceeding $250,000,000 (US$). Valve Software was in the process of developing Half-Life II (HL2), the widely-anticipated sequel to Half-Life, when their computer was "hacked" into or accessed without authorization. Based upon the sales of the original game, Valve Software had expected HL2 to generate sales revenue of at least $200,000,000. Valve Software learned of the unauthorized intrusion into its computer system on October 1, 2003, when the company became aware that an internal email from one Valve Software employee to another had been posted on a public website, and later, that programming code for HL2 and other Valve games had been stolen and released on different websites. Valve employee computer passwords were also posted. Since then, a working, unreleased version of HL2 and another Valve game have been circulated on the Internet. HL2 is now reportedly being sold on computer disks in Russia. As a result of all this activity, Valve Software began an in-depth review of the computers on their network and found at least thirteen machines that had been compromised within their network. Valve believes that the intrusion may have occurred as early as June 2003. The computers were provided to the FBI for further forensic analysis. Forensic analysts discovered a variety of "hacker" programs installed without Valve Software's permission. One allowed an intruder to capture passwords and other confidential information. Another program created a secure but unauthorized method of remote access, a "tunnel" for a hacker to use to sneak back into Valve's system. On one of Valve's networked computers, this program was configured to connect to the website "ago.gotdns.org." Like any other computer on the internet, the computer which contains the website "ago.gotdns.org" must have a unique Internet Protocol (IP) address so that Internet traffic sent from and directed to that computer is directed properly from its source to its destination. The IP address can be permanently assigned or dynamically assigned, meaning the computer is assigned a different IP address each time a new connection to the Internet is made. Either way, the IP Address used by a computer attached to the internet must be unique for the duration of the session, that is, from connection to disconnection. ISPs typically log their customers' connection, which means the ISP can, for a period of time, identify which of their customers were assigned a specific IP address during the time period of this session. In this case, the IP address of the website "ago.gotdns.org" was dynamically assigned. Although the IP addresses of this website during the 2003 intrusion into Valve's computer network are not known, the website remained active into 2004. It was checked regularly by investigators beginning in November of 2003, the last time on February 6, 2004. The IP addresses assigned to "ago.gotdns.org" during these checks are listed below in paragraph 3 of the request. The investigation has associated another website with "Ago." A posted message dated April 4, 2000, was found on a website identifying himself as Axel Gembe, with the email address [email protected], with the webpage "ago.daemon.sh." There is an important connection between the "ago.daemon.sh" website and the "ago.gotdns.ors" website. Both have dynamically assigned IP aggresses. When checked on the date and times listed in paragraph 1, the two webpages had the same IP address, which suggests both are on the same computer, the computer of the person who has the secure but unauthorized tunnel into a computer on Valve Software's computer network. After Valve Software discovered the intrusion on October, 2003, it asked the community of Half Life gamer and others to come forward with any information about those responsible. Two individuals, one anonymous, provided logs or transcripts of online communications known as "chat." In both, an individual claimed responsibility for the Valve Software intrusion and provided details consistent with the FBI's forensic analysis. In one of the chats, the individual identified himself as "ef~Ago." In the second chat log, dated October 11, 2003, the anonymous tipster identified the confessing hacker's IP Address as frb9_d9bb4a51.pool.Mediaways.net, which resolved to the numeric IP address 217.187.73.89 as of October 25, 2003. On February 16, 2004, U.S. authorities were contacted by Valve Software after the Chief Executive Owner (CEO) received an email from an individual claiming to have been the person who hacked into the Valve Software network. The individual used the following email address: [email protected]. That email address was provided by Hush Communications, a company located in Vancouver, Canada, which provides anonymous remailing services. The sender claimed to have had access to the Valve Software network for approximately six months. The sender then provided Valve Software with technical information "proving" he/she truly was the hacker. To date, these claims and details have been validated by the forensic analysis performed by both Valve Software and the FBI, and are also consistent with the details described in the chat logs previously provided to Valve Software. The sender continued to communicate with Valve's CEO, and is actively seeking work with or for Valve in connection with the security of its network. Requested Information: Please include the following information for each of the below requests if possible: Customer name (including all possible customers) Billing address and residential address Telephone number Any assigned network Internet Protocol address Records of session times and durations (beginning in June 2003) Length of service (including a start date) Type of services utilized (that is, DSL, cable modem, dial-up, web-hosting, e-mail, etc) Means and source of payment for such service (including any credit card or bank account information) Whether or not the IP Address is assigned dynamically or statically Any other information concerning the identity of the creator/subscriber, including but not limited to, other e-mail addressed, account profiles, date of birth, gender, or occupation Complete and accurate date and time stamps Please provide any available subscriber information, detailed above, for the users, assigned the IP address 217.187.73.89 and/or hostname frb9-d9bb4a51.pool.Mediaways.net, on October 11, 2003. Please provide any available subscriber information, detailed above, for the users assigned the e-mail address [email protected] Please provided any available subscriber information, detailed above, for the users assigne the following IP addresses and hostnames at associated times (Times are all Eastern Standard Time (EST); UTC/GMT - 5hours): Where the information cannot be provided, please preserve it until appropriate legal process can be obtained. Your consideration of this request is greatly appreciated.